Microsoft Defender for Storage in pills
Defender for Cloud is the Microsoft Cloud-Native Application Protection Platform (CNAPP) solution - the goal is to unify security and compliance analysis in a single platform to prevent, detect, and respond to cloud security threats.
Among the various plans that Defender for Cloud offers, there is Defender for Storage which analyzes data plane and control plane telemetry generated by Azure Blob Storage, Azure Files, and Azure Data Lake Storage services.
There are 3 key aspects of this product
Activity Monitoring
As all products in the Defender for Cloud suite, resource logs are monitored to identify anomalous and malicious behavior on storage: alerts relating to suspicious access patterns (Tor exit nodes, suspicious IP addresses/application/access), compromised tokens (suspicious token abuse/external operations, unusual access with tokens) and suspicious behavior (unusual data extraction/exploration/deletion operations). All this happens by exploiting the generation of a data model, statistical models, Microsoft Threat Intelligence and ML-based models.
Even if the operation of Defender for Cloud for Storage does not require the activation of logs for analysis, I recommend creating a diagnostic settings rule for log forwarding - for example by activating the connector for those using Microsoft Sentinel.
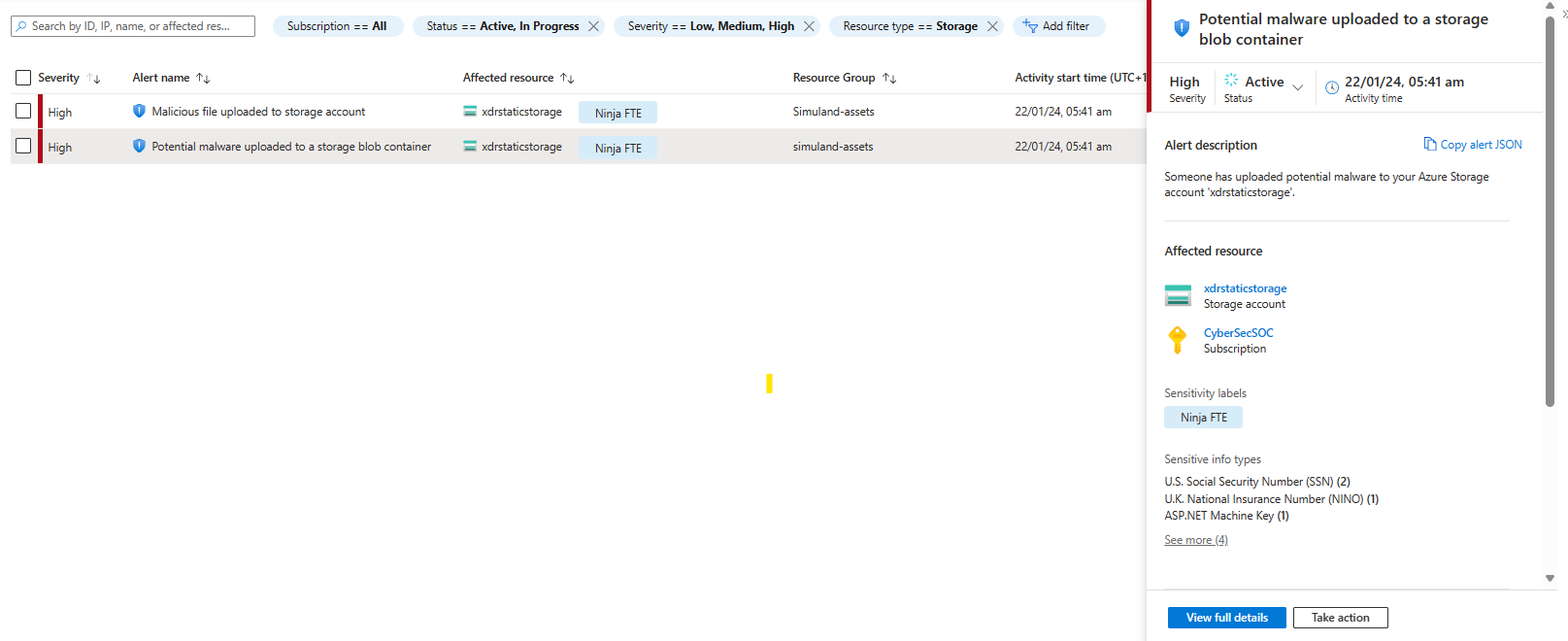
Some alerts raised by Defender for Storage:
- Access from a suspicious IP address
- Access from a known suspicious IP address to a sensitive blob container (Preview)
- Unusual amount of data extracted from a storage account
- Unusual amount of data extracted from a sensitive blob container (Preview)
- Potential malware uploaded to a storage account
- The access level of a sensitive storage blob container was changed to allow unauthenticated public access (Preview)
Sensitive data threat detection
This feature aims to identify sensitive content in Azure Blob Storage: an agentless solution is used. Scanning is carried out according to the following times
- when you enable Defender for Storage on new storage, results are generated within 24 hours
- when creating a new storage, the results are generated within 6 hours
- when the product is fully operational, a weekly scan is carried out
But what is meant by sensitive content? It all depends on what has been defined in Microsoft Purview: the Microsoft platform to govern and protect the data of the entire data assets!
Two important concepts from Microsoft Purview to understand its integration with Defender for Storage: sensitive information types and sensitivity labels. The first represents the content of the file (identified for example with automatic pattern recognition and/or ML) the second is a metadata associated with the file to understand its content without scanning it and applying restrictions accordingly: what links these two concepts for example is a data loss prevention policy, which assigns a sensitivity label based on the type of sensitive information in the file - we’ll talk about this in another blog post.
In Defender for Cloud there is a Data Security section where Sensitive data discovery is shown.
This feature is so powerfull, because:
- I can extend Purview functionality outside the cloud app based environment (not limited to Sharepoint/OneDrive/Box/Dropbox) - thus identifying that a storage has sensitive content
- I can better prioritize alerts - having insights shown on the alert page that describe the contents of the Storage. Note the alerts shown in the Activity Monitoring section that have the term sensitive.
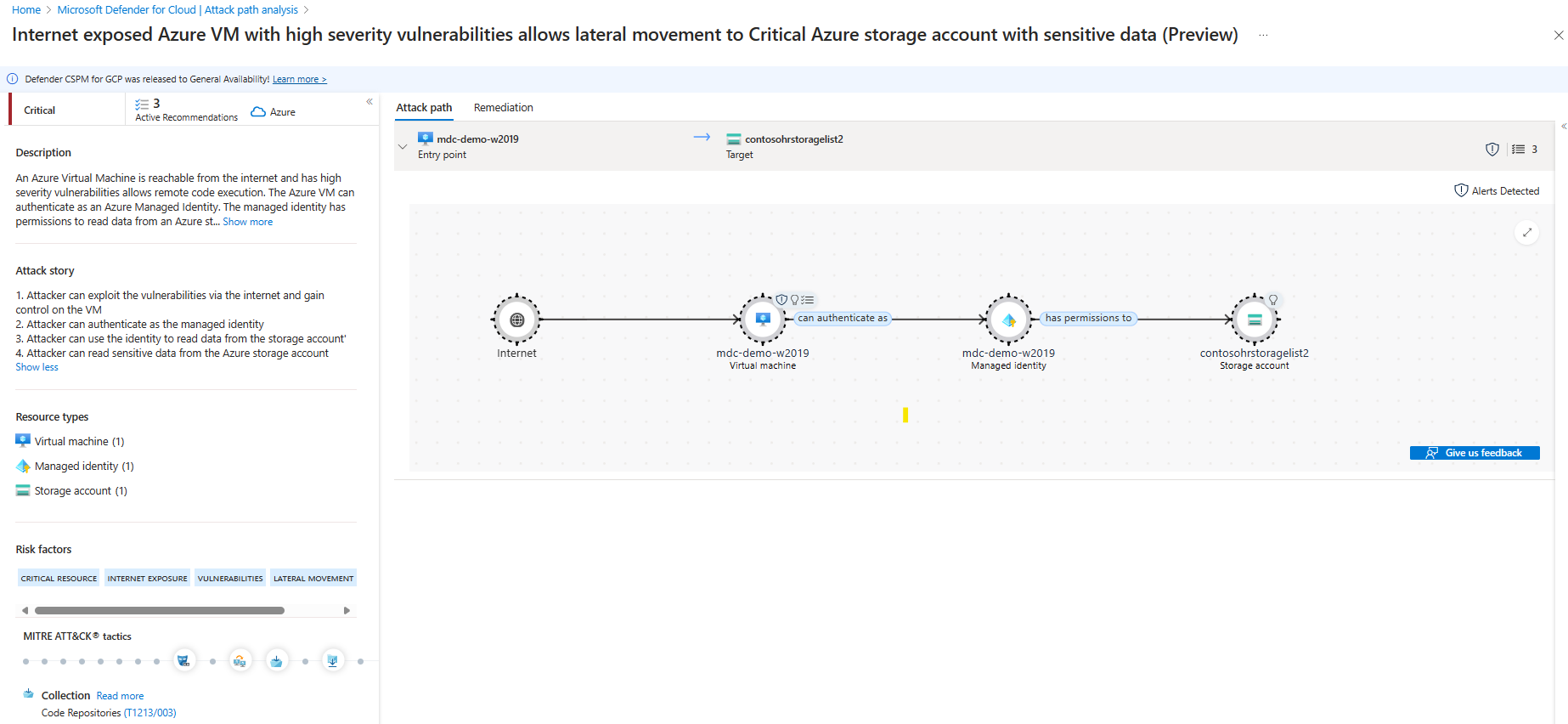
- Integration with Defender Cloud Security Posture Management (CSPM) - contextualizing resources and creating attack path analysis such as Internet exposed Azure VM with high severity vulnerabilities allows lateral movement to Critical Azure storage account with sensitive data (Preview)
Malware Scanning
This feature aims to identify malware (polymorphic and metamorphic) stored into storages - taking advantage of the Microsoft Defender Antivirus (MDAV) feature. As soon as a new file is uploaded to a storage, it is scanned to check whether it is malicious or not - the service is near real time, the duration of the scanning depends on several factors such as size, type and load on the service. The solution is agentless: the in-memory content is scanned, in the same region as where the storage account is deployed - and it is deleted as soon as it ends (for the more technical: a Data Scanner resource is created in Azure, and an Event topic Grid that reads blob upload trigger events).
It is possible to use the scan result in 4 different ways
- alerts in Defender for Cloud
Show yourself in the portal. Ability to start response workflows with Logic App. - logs forwarded to a Log Analytics Workspace (LAW) and saved in the StorageMalwareScanningResults table
If Sentinel is enabled in the LAW, it is possible to create Analytics Rules to raise ad hoc alerts - and any response workflows. - events published in an Event Grid topic
Published topic and consumed by one or more subscribers. Ability to have Function App that consumes the event. - Blob index tag
Key-value label associated with the blob that describes whether the content is healthy or not.
Note how Defender for Storage informs us about the malware but does not apply restrictions.
- How can we react?
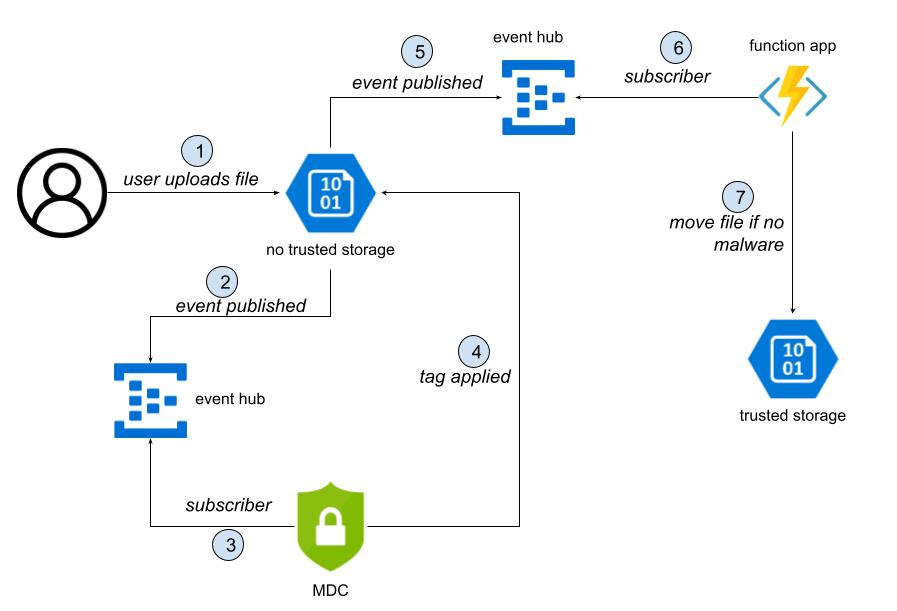
Here an example of a playbook that automatically deletes the file identified as malicious - Logic App triggered from the alert raised in Defender for Cloud. - How can it be prevented?
You can think of having two storage accounts: a temporary one in which the upload is carried out and the second which is the one used by the downloading applications. A file is moved from the first to the second if and only if it is not malicious. You can use an Event Grid Based approach with a Function App listening on the topic for the tag applied event.
Here an example of a Function App that consumes the tagging event.
The new Defender for Storage billing plan was released on March 28, 2023. The new plan is based on the number of protected storages, you can enable it at resource level too. Activity Monitoring and Sensitive data threat detection are included in the plan. Malware scanning in uploaded has a pricing that depends on how many GB are scanned.
For more information don’t hesitate to contact me!
Thank you for taking time to read.
Stay tuned!
Mario
